



Last year, a fake call centre in Georgia scammed more than 6,000 people out of about £27 million (≈ U.S. $35 million) by pretending to be trusted investment firms, according to The Guardian. Victims said the callers sounded calm, friendly, and professional, just like real advisers.
In another case reported by Ars Technica, a company employee in Hong Kong joined a video call with his company’s chief financial officer and team. But, he didn’t know every face on the screen was fake, created with AI. The result? He ended up sending U.S. $25 million to criminals.
These scams show how easily modern technology can turn a phone call or video chat into a trap. In the sections ahead, we’ll break down how these schemes/Blackhat Pay-Per-Call work, the warning signs to watch for, and simple steps to protect your business from the same kind of fraud.
Black hat pay-per-call is a marketing technique used to make money from phone calls. It relies on dishonest or illegal methods.
Rather than sending real customers to a business, black hat marketers use tricks such as fake calls, bots, misleading ads, or number spoofing to create calls that trigger a payout.
Their goal is to get paid for calls even when the caller is not interested or does not need the service.
This is risky. Marketers can be banned from ad networks, face legal action, and harm the businesses or people who answer those calls.
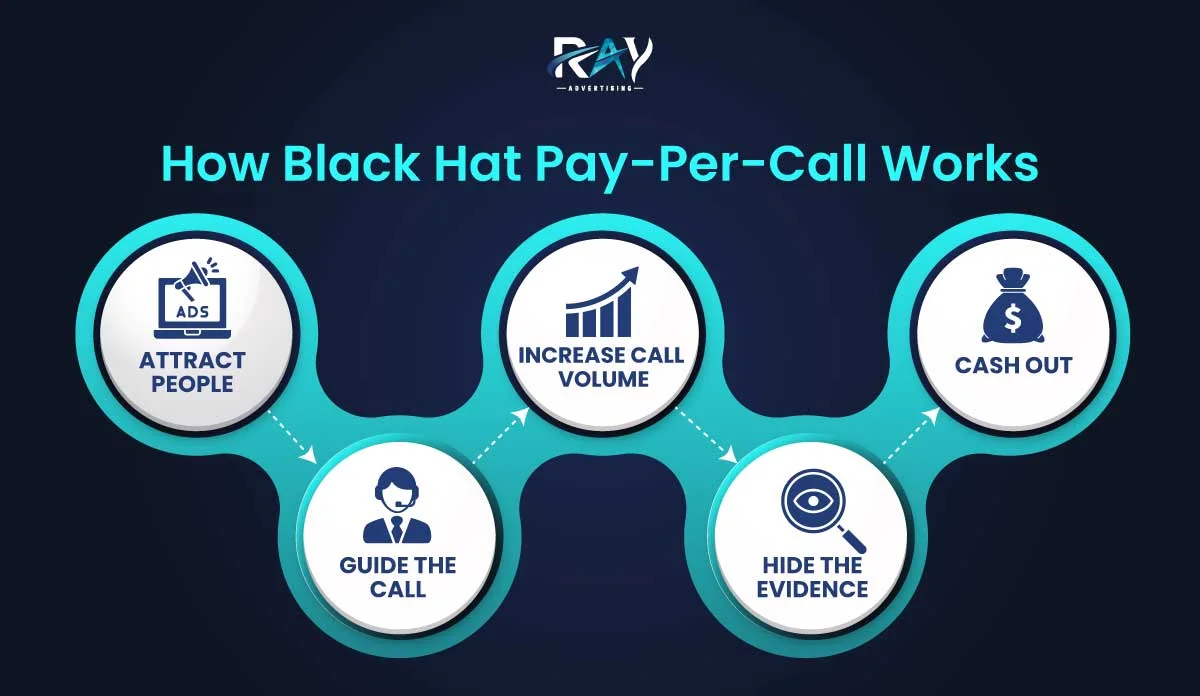
Most schemes are simple once you look at the flow. Someone pays to get a phone call counted as a lead. Black hat marketers then use tricks so the call looks real and get paid.
Here’s how it usually happens:
1. Attract people
They run ads or pop-ups that look trustworthy. Sometimes they use fake celebrity endorsements or false reviews.
2. Guide the call to count
When someone calls, the campaign makes sure the call meets the network’s rules for a paid lead. This means keeping the caller on the line long enough, navigating an automated menu, or reaching a required transfer step.
3. Increase call volume
Some operations hire bots or cheap call farms to place thousands of calls. Others spoof numbers to make the calls look local or trustworthy.
4. Hide the evidence
Scammers often cloak landing pages, falsify tracking, or route calls through multiple numbers. This makes it difficult for networks or advertisers to trace the real source.
5. Cash out and disappear
Once payouts arrive, money moves fast through shell companies and foreign accounts. That makes recovery hard.
Fake calls are phone calls made by software or automated systems that pretend to be real people. Scammers use them to create large numbers of “paid” calls so networks pay out for leads.
How it works
Warning signs
When bots can’t fool the system, black-hat marketers turn to real people. Call farms hire low-wage workers to make or take calls that look real enough to get paid. Click farms do the same for web actions that drive those calls.
How it works
Groups of workers sit in small offices or homes, each with a phone and a script. They call tracked numbers, press IVR options, and keep calls long enough to meet payout rules. Since they sound human, their calls can slip past basic fraud filters.
Warning signs
Number spoofing is when the phone number shown to callers is faked. Scammers make the caller see a local or trusted number while the call actually goes to a scam center. This tricks people into answering and lowers suspicion.
How it works
Fraudsters use services or weak carrier routes to change the displayed number. The call rings through to their line, but the caller thinks they are calling a known business or local number.
Warning signs
Call transfer abuse happens when callers are routed through multiple transfers so the final call counts for a payout, while the true endpoint or business is hidden. Fraudsters use this to make calls appear valid even if the real service or product isn’t involved.
How it works
Scammers design a call flow with several transfers. The caller thinks they are reaching a legitimate business, but the last transfer connects them to a line that earns the affiliate a payout. This hides the actual destination and increases the chance the call will be accepted as valid.
Warning signs
Fake tracking is when someone lies to the system that checks calls. They send false signals so the network thinks a real call or conversion happened. This trick gets platforms to pay for calls that never happened or were not valid.
How it works
A scammer changes the server messages that report a call. The network gets a message that says “call verified,” but the call may be fake, automated, or never happened. The network then pays out based on the fake report.
Warning signs
Affiliate or publisher fraud is when the same caller or lead is sold more than once, or old leads are resubmitted to earn multiple payouts. It steals money from buyers and hides the true value of traffic.
How it works
An affiliate collects a lead or call and then sells that same contact to different buyers. Or they resubmit a previously paid lead as if it were new. Networks pay for each reported conversion. Over time, a single person can generate several payouts.
Warning signs
Cloaking is when a site shows one page to reviewers or crawlers and a different page to real visitors. The live page pushes people to call a tracked number or hides the true offer. This helps fraudsters hide scams from platforms and auditors.
How it works
A bot or crawler sees a normal, safe page. A real visitor sees a page designed to get them to call. The two versions can be very different while sharing the same URL.
Warning signs
Scammers create fake voices or video faces to sound or look like someone the target trusts. The goal is to lower a person’s guard so they follow instructions or share money.
How it works
Fraudsters collect real audio or video of a person. Then they make an AI copy that speaks or moves like the real person. The scammer plays the fake voice or shows the fake video during a call or meeting. The target believes the caller is real and acts on the request.
Warning signs
Ad injection is when scammers place ads on websites without the site owner’s permission. The ads push visitors to call tracked numbers, often leading to fraudulent pay-per-call payouts.
How it works
Malicious scripts or third-party services insert ads into popular websites. Visitors see the ad, click it, and are directed to a page or number controlled by the scammer. The publisher never placed the ad, but the call appears legitimate to the network.
Warning signs
Domain spoofing is when scammers make a website look like a trusted publisher or brand to trick visitors. The goal is to make calls appear legitimate and hide the real source.
How it works
Fraudsters copy or fake a domain so it looks identical or very similar to a real site. Visitors think they are on a trusted page, click a number, and the call goes to a scam line. Networks see it as valid traffic.
Warning signs

Black-hat pay-per-call schemes can cost your business money, damage your reputation, and create legal headaches. Focus on these core protections:
Tired of risky campaigns that waste money or get you banned?
With Ray Advertising’s pay-per-call marketing, you get real customers, verified calls, and transparent tracking. Every call counts toward growing your business safely.
Take control of your leads. Grow your business the smart way, without the scams.
Black-hat pay-per-call can waste money, damage a business’s reputation, and create legal problems. Recognizing common tricks and warning signs keeps businesses safe. Honest, verified methods make sure calls come from real customers and deliver real results.
How to Create High-Converting Landing Pages for Af...
February 26, 2026
Boosting Affiliate Marketing with Behavioral Targe...
February 23, 2026
How to Earn with Affiliate Marketing Content...
February 19, 2026
Why You Should Consider Using Native Ads in Your A...
February 7, 2026

Voice Search and Affiliate Marketing: What to Know...
January 29, 2026

Affiliate Marketing Strategies for Health & Wellne...
January 29, 2026

How to Use Podcasting for Affiliate Marketing in 2...
January 29, 2026

How to Use YouTube Videos for Pay-Per-Call Marketi...
January 29, 2026

How to Become an Affiliate Marketer: A Step-by-Ste...
January 29, 2026